Strategies to help you manage the difficult situations that developers face at work. Perhaps the best inspiration for a practical developer was shared by Sundar Pichai, Google CEO in his famous cockroach theory. A cockroach? Yes, you heard that right!
-
-
Javadoc Coding Standards
Javadoc is a key part of coding in Java, yet there is relatively little discussion of what makes good Javadoc style - a coding standard.
-
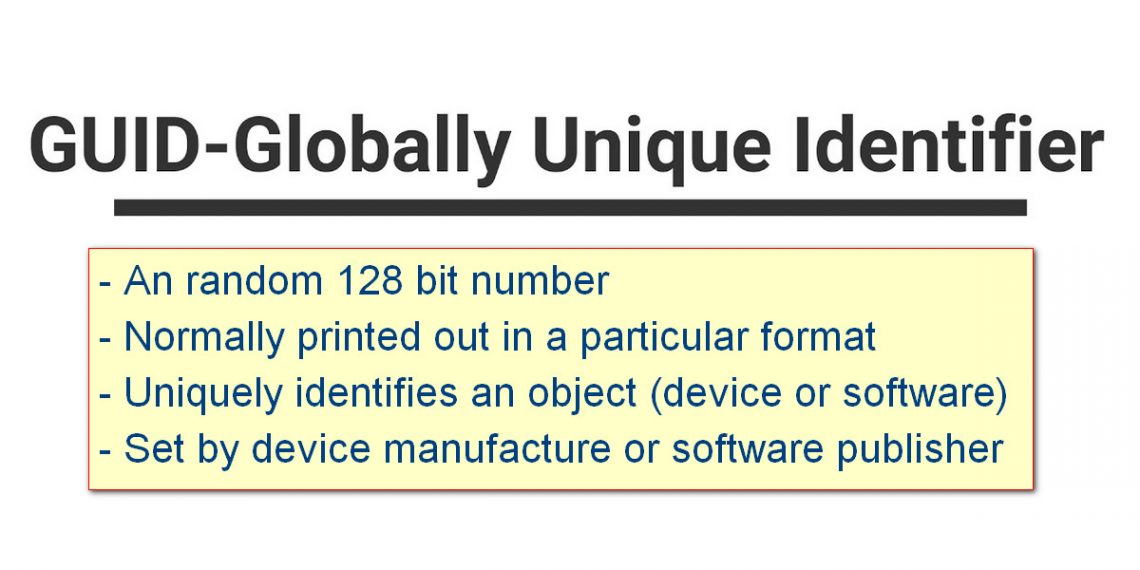
Understanding Globally Unique Identifier (GUID)
Short for Globally Unique Identifier, a unique 128-bit number that is produced by the Windows OS or by some Windows applications to identify a particular component, application, file, database entry, and/or user. For instance, a Web site may generate a GUID and assign it to a user's browser to record and track the session. A GUID is also used in a Windows registry to identify COM DLLs. Knowing where to look in the registry and having the correct GUID yields a lot information about a COM object (i.e., information in the type library, its physical location, etc.). Windows also identifies user accounts by a username (computer/domain and username) and assigns…
-
Basics of Internet Cookies
Cookies can help provide a unique and tailored user experience. But what are the different types of cookies? What are they used for? Can be the deleted or blocked? Read this guide to find out more about cookies and how they affect you.
-
What is URL Encoding and How does it work?
You may think that a "valid" URL is self-evident, but that's not quite the case. A URL entered within an address bar in a browser, for example, may contain special characters (e.g. "上海+中國"); the browser needs to internally translate those characters into a different encoding before transmission. By the same token, any code that generates or accepts UTF-8 input might treat URLs with UTF-8 characters as "valid", but would also need to translate those characters before sending them out to a web server. This process is called URL-encoding or percent-encoding.
-
Secure Shell
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line login and remote command execution, but any network service can be secured with SSH. SSH provides a secure channel over an unsecured network in a client–server architecture, connecting an SSH client application with an SSH server. The protocol specification distinguishes between two major versions, referred to as SSH-1 and SSH-2. The standard TCP port for SSH is 22. SSH is generally used to access Unix-like operating systems, but it can also be used on Microsoft Windows. Windows 10 uses OpenSSH as its default SSH client. SSH was designed…
-
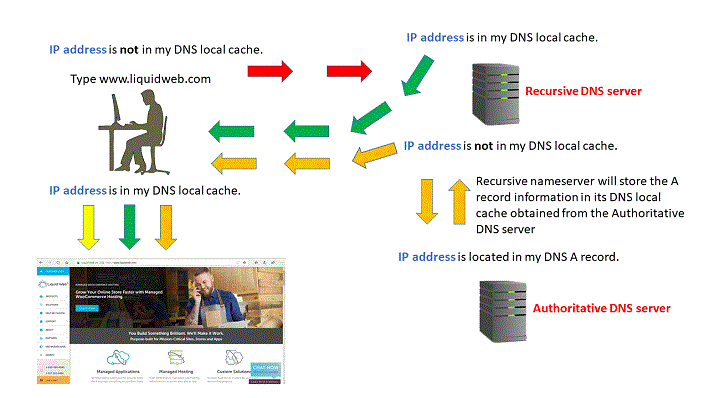
Understanding the DNS Process
Do you ask yourself, “What is DNS?” “Do I need to use DNS?” Do you feel confused? In some cases, DNS can be convoluted and complicated. Let’s talk about Domain Name System (DNS) services. When you need to access a website, you type the domain name, such as www.google.com, into the web browser instead of typing an IP address. A conversion happens between www.google.com to 172.217.12.46, an IP, which designated to a device on the Internet. This conversion is a DNS query, an integral part of devices connecting with each other to communicate over the internet. To understand the DNS query process, let’s talk about how a DNS query routes…
-
System Architecture of SAP Commerce Accelerator
Commerce Accelerator combines a feature-rich web application with a collection of software components that fulfill many typical use cases that are common requirements on a vast number of SAP Commerce implementation projects. This document helps you understand the software as well as understand in more detail the features implemented by the software, how everything fits together, and how you can adapt the code or configure it to fulfill your project's requirements.
-
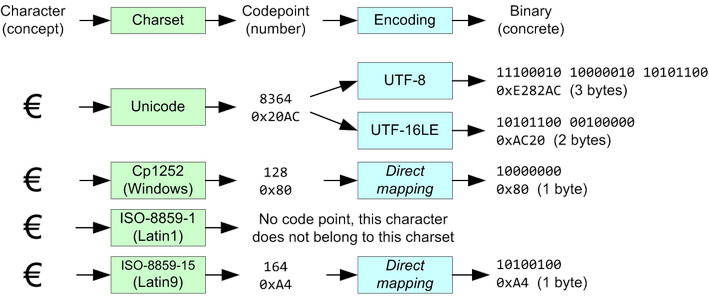
Introducing Character Sets and Encoding
If you are dealing with text in a computer, you need to know about encodings. Period. Yes, even if you are just sending emails. Even if you are just receiving emails. You don't need to understand every last detail, but you must at least know what this whole "encoding" thing is about. And the good news first: while the topic can get messy and confusing, the basic idea is really, really simple.
-
Complexity of an algorithm
In computer science, the complexity of an algorithm is a way to classify how efficient an algorithm is, compared to alternative ones. The focus is on how execution time increases with the data set to be processed. The computational complexity and efficient implementation of the algorithm are important in computing, and this depends on suitable data structures.