Discovering one’s “purpose” in life is not about some great achievement, but merely finding a way to spend your limited amount of time well.
-
-
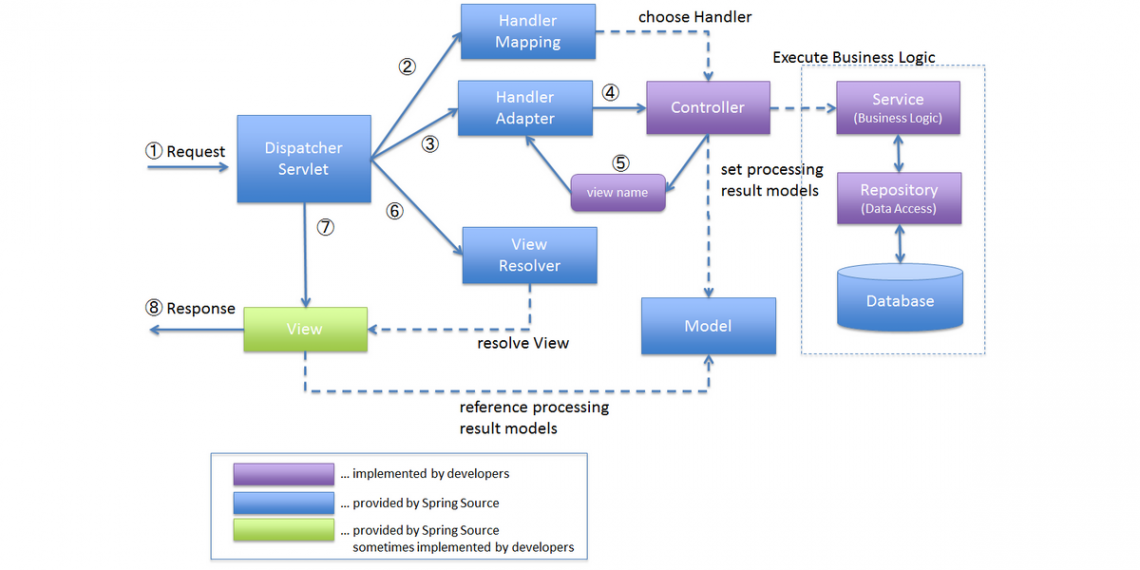
14 Tips for Writing Spring MVC Controllers
In this article, I'm going to share with you some of the fundamental techniques and best practices for writing a controller class with the Spring MVC framework. Typically, in Spring MVC, we write a controller class to handle requests coming from the client. Then, the controller invokes a business class to process business-related tasks, and then redirects the client to a logical view name, which is resolved by Spring’s dispatcher servlet in order to render results or output. That completes a round trip of a typical request-response cycle.
-
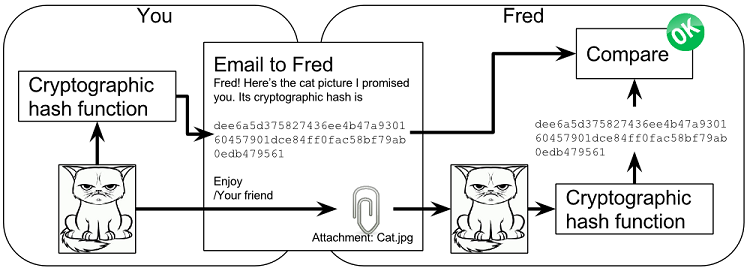
What is checksum and how to calculate and use checksum values to verify data and file integrity
Cryptographic hashes You can think of a cryptographic hash as a fingerprint. A person produces the same fingerprint of her left thumb every time it’s taken, but it’s difficult to find another person with the same left thumb fingerprint. The fingerprint doesn’t disclose any information about the person other than her left thumb fingerprint. You can’t know what math skills she has or what eye color she has by looking at her fingerprint. A fingerprint of a file is called a cryptographic hash. To create a cryptographic hash of a file, you send the file into a computer program called a cryptographic hash function. Why are cryptographic hash functions useful? Cryptographic…