Strategies to help you manage the difficult situations that developers face at work. Perhaps the best inspiration for a practical developer was shared by Sundar Pichai, Google CEO in his famous cockroach theory. A cockroach? Yes, you heard that right!
-
-
Javadoc Coding Standards
Javadoc is a key part of coding in Java, yet there is relatively little discussion of what makes good Javadoc style - a coding standard.
-
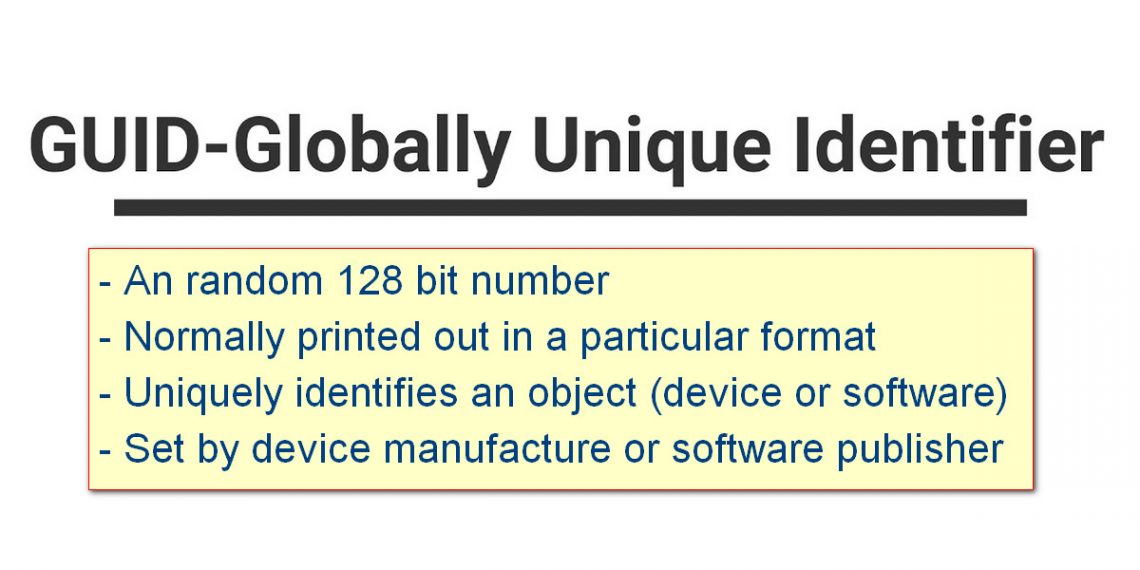
Understanding Globally Unique Identifier (GUID)
Short for Globally Unique Identifier, a unique 128-bit number that is produced by the Windows OS or by some Windows applications to identify a particular component, application, file, database entry, and/or user. For instance, a Web site may generate a GUID and assign it to a user's browser to record and track the session. A GUID is also used in a Windows registry to identify COM DLLs. Knowing where to look in the registry and having the correct GUID yields a lot information about a COM object (i.e., information in the type library, its physical location, etc.). Windows also identifies user accounts by a username (computer/domain and username) and assigns…
-
Basics of Internet Cookies
Cookies can help provide a unique and tailored user experience. But what are the different types of cookies? What are they used for? Can be the deleted or blocked? Read this guide to find out more about cookies and how they affect you.
-
Unit Test Naming Convention
How many times have you run your tests, gotten a failure, and had to go digging through the test code to try to understand what it’s complaining about? For many of you, you’re so used to doing this that you don’t even notice it’s a problem.
-
Preparing for a Software Developer Interview
After working for quite some time at the same company, you decide it’s time to look around for another job. And there’s nothing wrong with that. You want to develop yourself as a person, but you’re also looking for a great opportunity to develop your skillset. Preferably, in a whole different environment. So, you start looking for job applications on the internet. After spending hours looking for the perfect job application, you finally found it. The job hunt was successful. This has got to be the one! You decide to not waste any more time and you start writing your motivational letter. Obviously, you are the most suitable candidate for…
-
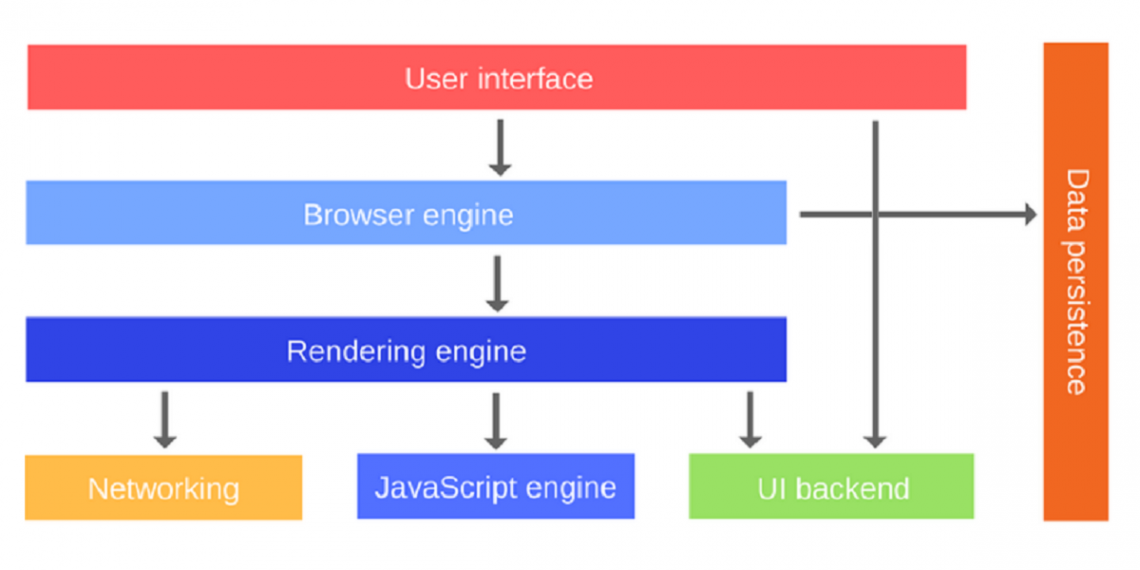
Major components of a web browser
When you’re building web apps, however, you don’t just write isolated JavaScript code that runs on its own. The JavaScript you write is interacting with the environment. Understanding this environment, how it works and what it is composed of will allow you to build better apps and be well-prepared for potential issues that might arise once your apps are released into the wild.
-
What is URL Encoding and How does it work?
You may think that a "valid" URL is self-evident, but that's not quite the case. A URL entered within an address bar in a browser, for example, may contain special characters (e.g. "上海+中國"); the browser needs to internally translate those characters into a different encoding before transmission. By the same token, any code that generates or accepts UTF-8 input might treat URLs with UTF-8 characters as "valid", but would also need to translate those characters before sending them out to a web server. This process is called URL-encoding or percent-encoding.
-
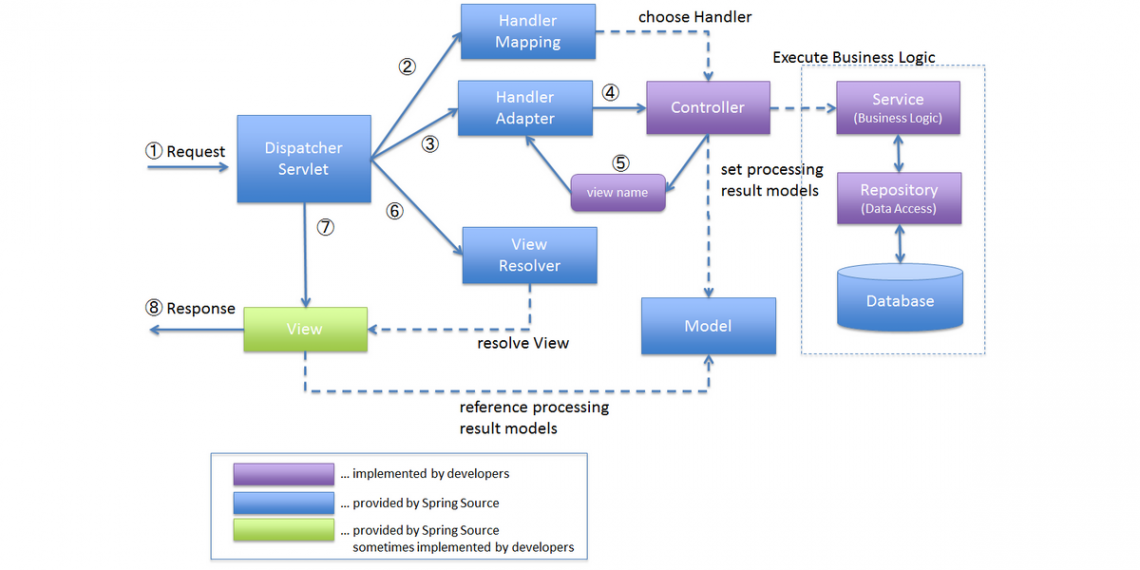
14 Tips for Writing Spring MVC Controllers
In this article, I'm going to share with you some of the fundamental techniques and best practices for writing a controller class with the Spring MVC framework. Typically, in Spring MVC, we write a controller class to handle requests coming from the client. Then, the controller invokes a business class to process business-related tasks, and then redirects the client to a logical view name, which is resolved by Spring’s dispatcher servlet in order to render results or output. That completes a round trip of a typical request-response cycle.
-
3 Main Types of Encryption
References https://medium.com/@peterchang_82818/review-3-main-types-of-encryption-hash-symmetric-asymmetric-tutorial-example-understand-5e57c290324c https://www.geeksforgeeks.org/rsa-algorithm-cryptography/ https://butchiso.com/2016/01/ma-hoa-bat-doi-xung-rsa.html https://hackernoon.com/generating-rsa-private-and-public-keys-b82a06db6d1c https://vakaxa.com/vi/private-key-la-gi-public-key-la-gi-su-khac-biet-giua-private-key-va-public-key/ https://hackernoon.com/how-does-rsa-work-f44918df914b