Discovering one’s “purpose” in life is not about some great achievement, but merely finding a way to spend your limited amount of time well.
-
-
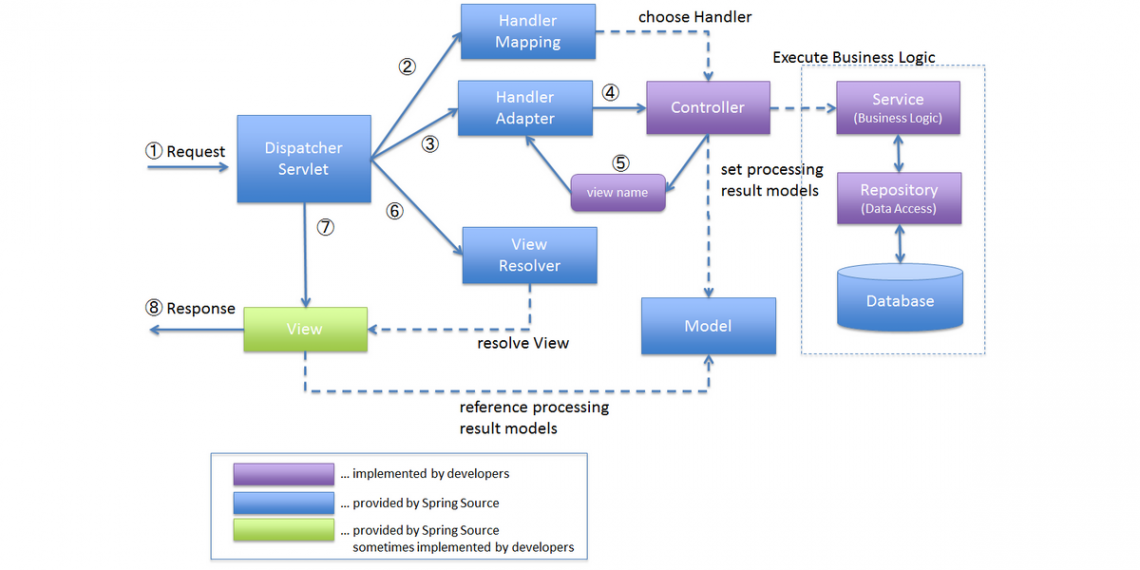
14 Tips for Writing Spring MVC Controllers
In this article, I'm going to share with you some of the fundamental techniques and best practices for writing a controller class with the Spring MVC framework. Typically, in Spring MVC, we write a controller class to handle requests coming from the client. Then, the controller invokes a business class to process business-related tasks, and then redirects the client to a logical view name, which is resolved by Spring’s dispatcher servlet in order to render results or output. That completes a round trip of a typical request-response cycle.
-
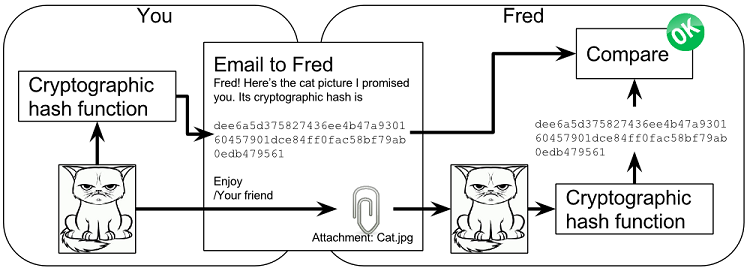
What is checksum and how to calculate and use checksum values to verify data and file integrity
Cryptographic hashes You can think of a cryptographic hash as a fingerprint. A person produces the same fingerprint of her left thumb every time it’s taken, but it’s difficult to find another person with the same left thumb fingerprint. The fingerprint doesn’t disclose any information about the person other than her left thumb fingerprint. You can’t know what math skills she has or what eye color she has by looking at her fingerprint. A fingerprint of a file is called a cryptographic hash. To create a cryptographic hash of a file, you send the file into a computer program called a cryptographic hash function. Why are cryptographic hash functions useful? Cryptographic…
-
3 Main Types of Encryption
References https://medium.com/@peterchang_82818/review-3-main-types-of-encryption-hash-symmetric-asymmetric-tutorial-example-understand-5e57c290324c https://www.geeksforgeeks.org/rsa-algorithm-cryptography/ https://butchiso.com/2016/01/ma-hoa-bat-doi-xung-rsa.html https://hackernoon.com/generating-rsa-private-and-public-keys-b82a06db6d1c https://vakaxa.com/vi/private-key-la-gi-public-key-la-gi-su-khac-biet-giua-private-key-va-public-key/ https://hackernoon.com/how-does-rsa-work-f44918df914b
-
Secure Shell
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line login and remote command execution, but any network service can be secured with SSH. SSH provides a secure channel over an unsecured network in a client–server architecture, connecting an SSH client application with an SSH server. The protocol specification distinguishes between two major versions, referred to as SSH-1 and SSH-2. The standard TCP port for SSH is 22. SSH is generally used to access Unix-like operating systems, but it can also be used on Microsoft Windows. Windows 10 uses OpenSSH as its default SSH client. SSH was designed…
-
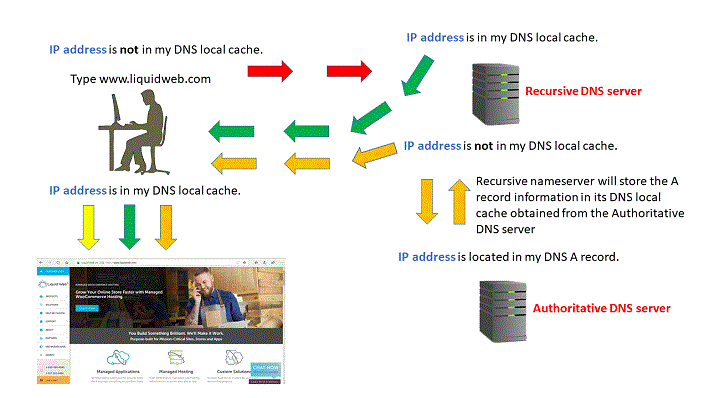
Understanding the DNS Process
Do you ask yourself, “What is DNS?” “Do I need to use DNS?” Do you feel confused? In some cases, DNS can be convoluted and complicated. Let’s talk about Domain Name System (DNS) services. When you need to access a website, you type the domain name, such as www.google.com, into the web browser instead of typing an IP address. A conversion happens between www.google.com to 172.217.12.46, an IP, which designated to a device on the Internet. This conversion is a DNS query, an integral part of devices connecting with each other to communicate over the internet. To understand the DNS query process, let’s talk about how a DNS query routes…
-
System Architecture of SAP Commerce Accelerator
Commerce Accelerator combines a feature-rich web application with a collection of software components that fulfill many typical use cases that are common requirements on a vast number of SAP Commerce implementation projects. This document helps you understand the software as well as understand in more detail the features implemented by the software, how everything fits together, and how you can adapt the code or configure it to fulfill your project's requirements.
-
Notepad++ tips
Notepad++ is a text editor and source code editor for use with Microsoft Windows. It supports tabbed editing, which allows working with multiple open files in a single window. The project's name comes from the C increment operator.
-
PowerShell in Action
PowerShell is a task-based command-line shell and scripting language built on .NET. PowerShell helps system administrators and power-users rapidly automate tasks that manage operating systems (Linux, macOS, and Windows) and processes. PowerShell commands let you manage computers from the command line.
-
Integrating Solr with PHP
Solr has quickly become one of the most popular search engines available. Due to Solr’s many features and its low barrier to entry it can be an ideal candidate when seeking a search engine.